What Is Cloud Infrastructure Entitlements Management (CIEM)?
Cloud Infrastructure Entitlements Management (CIEM) is the security process of managing access rights, permissions, or privileges for the identities of a single or multi-cloud environment. This process helps to identify and avoid risks resulting from privileges being higher or broader than they should.
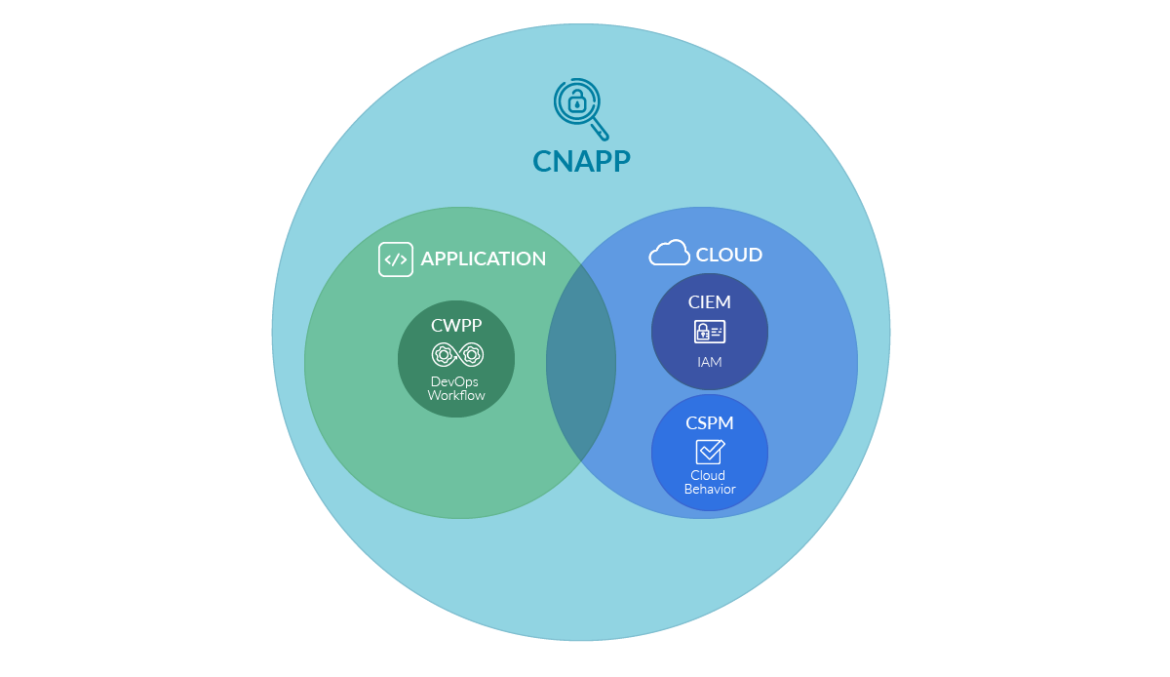
Furthermore, CIEM is one of the processes of the Cloud-native application protection platform (CNAPP), a security process that takes CIEM with CSPM and CWPP, other processes, to upgrade its features because these were insufficient to completely secure the cloud alone.
What Is CIEM?
What you’ll learn
-
The difference between an IAM and a CIEM
-
How a CIEM works and why it’s a fundamental part of modern CDR
-
How to choose the ideal CIEM solution
It’s possible that reading such a technical introduction might not have provided clarity as to why use CIEM, so let’s start with something easier:
- Does your system have overpowered identities that are not used anymore?
- Maybe the overpowered identities are those that are habitual in your cloud environment.
- Are you sure what privileges you are giving to third parties in your system?
- Is there an impostor code among us?
Whether you are a veteran CISO or new in managing privileges in the cloud, stick with us and we’ll show you why it’s crucial to start having CIEM in mind.
Why is CIEM important?
Imagine that you have a cloud environment. On this, you have many users, automated software, or, as they are known, identities. You also have some resources (data, services, etc.) on it.
Now, imagine that some of these resources have to be restricted, or that you have to create an identity hierarchy along your resources, therefore bringing privileges to your identities.
This can be fully solved with an IAM service that can help you manage these privileges for your cloud environment identities. But hold on, what if…
- For no reason, one of your identities is working as it shouldn’t?
- Something or someone is doing what it wasn’t supposed to?
- There is actually a reason and you weren’t aware of it?
While IAM will manage and have a register of these privileges without checking if some are broken or overpowered, CIEM will check these and modify them if it’s necessary.
CIEM challenges
In order to ensure that the identities actions are what are supposed to be, a CIEM solution can have different approaches for an issue:
- Inactive identities and super identities: A cloud environment can have unused identities that could have compromising privileges or access rights for the environment, which sometimes can be unlimited to the cloud resources.
- Overpowered active identities: Otherwise, some active identities can have higher permissions than they should.
- Cross-account access: In some situations, it could be necessary to create accounts (cross-account or IAM roles) that allow identities or third parties to access different resources of the cloud (for development, testing, production, etc.). Misconfigured or overpowered account privileges could compromise the entire infrastructure.
- Machine identities unauthorized access: A nonhuman identity is designed to perform a controlled sequence of actions, unless it’s changed. If the behavior or results of the nonhuman identity changes unexpectedly, maybe someone has altered the internal design or is injecting outside actions.
Benefits of using CIEM
There are different CIEM challenges and approaches. Based on these, CIEM is a solution that brings several benefits in a centralized way, independent of whether your cloud is a single environment or multi-cloud one:
- Compliance: CIEM will monitor all your cloud or multi-cloud identities and check if each one complies with its given privileges, as well as if these privileges meet the compliance requirements and standards.
- Detection and remediation: CIEM will detect any unexpected behaviors that involve misconfigured or bypassed privileges and remediate them automatically over your different clouds.
- Governance: CIEM will monitor your identities along your different cloud environments and verify that these accomplish its defined governance.
- Visibility: CIEM allows you to view all of your identities and privileges in one place, whether from one cloud or different ones.
How does CIEM work?
Considering the benefits, how does CIEM put them in practice? Apart from being a solution that brings all the information and executions in a centralized place among your clouds, it is also a solution based on a continuous “match, check and remediation” method and the CIEM lifecycle.
What does the “match, check and remediation” method mean? In order to monitor your cloud, the CIEM solution has to access the information of it:
- Initially, the CIEM solution will request two types of information to the IAM service that is based on:
- Cloud identities: Anything that can access your cloud services or resources. These can be human (user, administrator, developer) or non-human (software, external device) identities.
- Cloud entitlements: Once the CIEM has the identity, it will get its entitlements – that means the tasks and the access privileges that the identity is supposed to have.
- The identities requested and the entitlements can vary depending on the situation and the motive of the monitorization.
- Once it gets the identity and the entitlements, CIEM will verify the behavior and the actions of the identity contrasting them against the entitlements.
- If there is suspicious activity that bypasses any of the given privileges, CIEM will remediate it by removing all the privileges, deactivating the identity, or lowering its privileges in the IAM service.
- Once CIEM finishes, it will repeat the same steps continuously.
CIEM Lifecycle
CIEM also works based on the Principle of least privilege (POLP) to manage identities’ private and public cloud permissions. Then it can minimize and mitigate any possible risk of excessive privilege, such as cloud leaks, data breaches, or insider threats.
The POLP, or the access control principle or the principle of minimal privilege, is a concept in computer security that states that you should limit any user access rights to only what is strictly necessary to do the job.
To provide an scalable enforcement of POLP across the cloud, CIEM solutions have the CIEM Lifecycle, the framework that every CIEM solution has to follow:
- Account and entitlement discovery: CIEM solution must continuously search and list every existing entitlement in the cloud to properly apply the least privilege.
- Cross-cloud entitlement correlation: In general, the cloud environment will be multi-cloud, so the solution must provide consistent mechanics for entitlement policies across the different clouds.
- Entitlement visualization: The solution must allow the visualization of the different entitlements of the cloud and its accesses, or filtering through specific entitlement or access type.
- Entitlement optimization: The solution must also, besides searching for new entitlements, regulate entitlement privileges and remove those that can be excessive, reducing the attack surface but also giving the minimum, as the least privileges states.
- Entitlement protection: The solution could detect when an entitlement’s access has changed and alert the possibility of a threat (e.g., privilege escalation). It should also provide optionally configurable rulesets to define the entitlement guardrails to be enforced in the cloud environment.
- Entitlement detection: The solution must also have the ability to detect any suspicious activity at the moment of monitoring the entitlements (for searching, optimizing, etc).
- Entitlement remediation:The solution must support multiple means of remediation.
How do I choose my CIEM solution?
Once you know why it is important and how it works, ask yourself…
How do I choose my CIEM solution?
But before thinking about it, why not ask…
Do I really need CIEM?
There isn’t a checklist or a standard guide that will help you decide if it’s really necessary or not. This decision is up to you, but here we will leave some use cases that can help you decide:
- You could use CIEM if:
- You want a sandbox environment for developing things and test functionalities.
- You have a cloud environment where there are a huge number of identities.
- You have a multi-cloud environment and you want to monitor every identity in a single place, although there are few of them.
- You want an automated management and monitor of the privileges, although there are few identities.
- You want to apply compliance standards.
- You couldn’t use CIEM if:
- You have a cloud environment where there aren’t too many identities, and it isn’t very crowded. Then, you can work with IAM instead.
- You have a cloud environment that is private for your own use.
Once you have decided if you really need a CIEM solution, now you have to compare different solutions to choose which fits better to your cloud. There isn’t any standardized checklist or guideline that will tell you which solution will be better or worse.
A good approach is taking the CIEM lifecycle and studying which requirements your cloud environment has and which of them could be fulfilled with a CIEM solution. Then, you can select different solutions and verify in which needs the solutions are stronger or weaker against each other, and select your preferred one.
What did you learn today?
CIEM grants, resolves, enforces, or revokes the access rights or privileges of all the identities, human or nonhuman, in a cloud system. That limits what they can do or where they can go, with the objective of mitigating the risks resulting from misconfigured permissions levels.