Happy New Year! My name is Zain Ghani. I’m a Customer Solutions Architect based in Austin, Texas, and I’m excited to share our latest updates with you.
This year started with multiple recognitions for Sysdig. GigaOM named Sysdig a Leader and the only Outperformer in its inaugural Cloud Workload Security Radar report. The report compares major players in the space and highlights the evolution of the cloud security market “driven by the need for robust, feature-rich platforms capable of addressing diverse and complex security needs.”

Sysdig is also honored to receive the DevOps Dozen 2023 award as the 𝗕𝗲𝘀𝘁 𝗖𝗹𝗼𝘂𝗱 𝗡𝗮𝘁𝗶𝘃𝗲 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗦𝗼𝗹𝘂𝘁𝗶𝗼𝗻.
“Security teams must protect the business without slowing it down. Sysdig continues to be an innovative market leader. We are proud to honor them with this year’s cloud-native security provider award.”
Alan Shimel, Techstrong Group Founder & CEO

Stay tuned for more updates from Sysdig, and let’s get started!
Sysdig Secure
Data Types for Events Forwarding
Sysdig’s Events Forwarding feature now supports Activity Audit. Additionally, we have initiated deprecation for the following legacy data types:
- Legacy Runtime policy event format, replaced by the new format
- Legacy Compliance v1 events (Secure events compliance and Benchmark events), part of the Legacy compliance
- Legacy Vulnerability Scanner v1, part of the Legacy scanning engine
Filter for Updated Threat Detection Rules
We have added a new drop-down filter on the Rules Library page to easily review recent changes made to rules and exceptions.
See View Recent Changes to a Rule for details.
Introducing Infrastructure as Code Scanning Integration to Sysdig CLI Scanner
Sysdig is thrilled to announce a major advancement to the sysdig-cli-scanner tool with the integration of Infrastructure as Code (IaC) scanning functionality. This release empowers users to seamlessly scan IaC resources for potential risks and compliance issues, enhancing the security posture of your development workflows. By using the familiar sysdig-cli-scanner interface, you can initiate IaC scans to identify potential risks and compliance issues early in the development lifecycle. The tool continues to support the basic functionality.
Key features:
- A comprehensive exit code system for easy interpretation of scan results
- Role-Based Access Control (RBAC) for precise control over permissions
- Cross-platform compatibility
- Ability to integrate into existing workflows, such as CI/CD pipelines
- Use of API Token for authentication, ensuring consistency with the VM CLI
- Simple command execution
For more information, see Run Sysdig CLI Scanner in IaC Mode.
Inventory (General Availability)
Sysdig is pleased to make our Inventory feature available by default to all Secure SaaS customers with the following capabilities:
- Unified Data: Leveraging our Cloud Attack Graph to combine posture, vulnerability, configuration, and network exposure findings, as well as Runtime Insights on your resources
- “Featured Filters” panel: Improved search experience
- Image as a Resource: Container images are returned as a first-class citizen
- Image and Workload Vulnerabilities: View and search on vulnerability data (CVE, Package, Exploit, Fix, In Use, etc.)
- Network Exposure on Vanilla K8s Workloads, AWS EC2s and S3 buckets, Azure VMs, and Blob Containers: Display and query resources that are directly or ingress-exposed to the internet
- New resource metadata is available:
- Search for Containers and Image Pullstrings on K8s Workloads
- Search by Namespace for IaC K8s Workloads
- Search for cloud resources by ARN for AWS or Resource ID for GCP and Azure
- Unique URL for each resource (in addition to applied search filters) which can be shared with your teammates/colleagues
See Inventory for details.
Improved Jira Integration
Vulnerability Management (VM) has now been fully integrated with Jira. Click on any vulnerability in the VM module to create a fully-fleshed out Jira ticket, which you can assign to a colleague from the comfort of the Sysdig UI. Sysdig will then remember which vulnerabilities have Jira tickets.
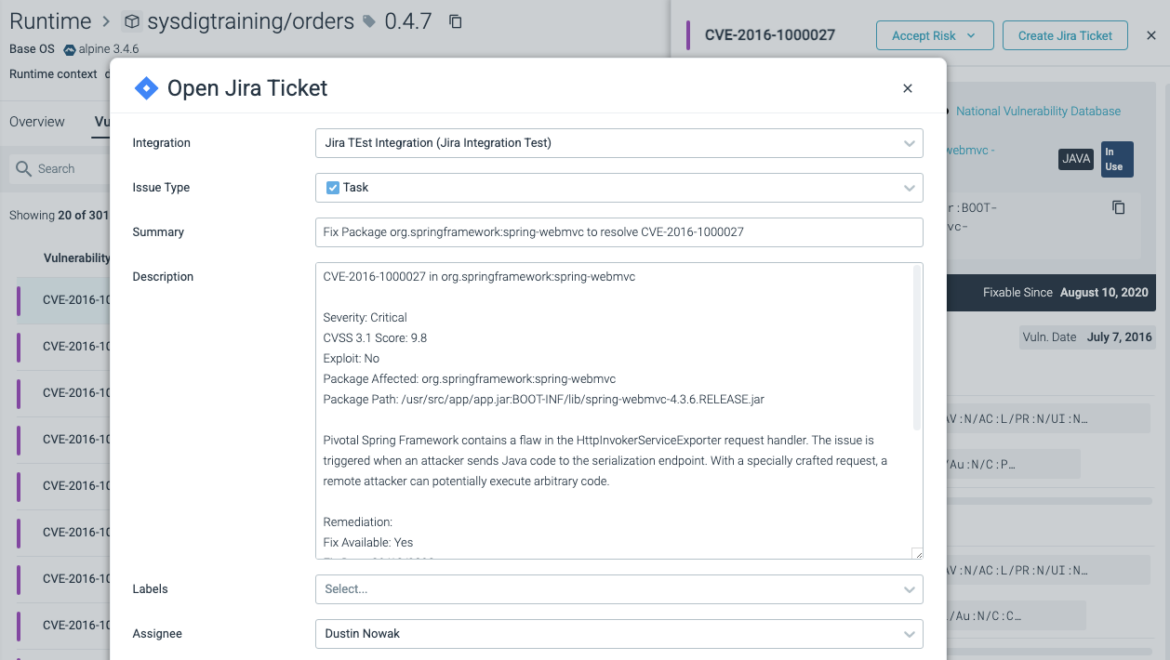
See Remediate with Jira for details.
Splunk Integration
Splunk has been integrated with Vulnerability, joining the ranks of Jenkins and ServiceNow. Fetch, triage, and orchestrate Sysdig runtime vulnerabilities in Splunk with a Technical Add-On (TA). The Splunk TA enables the extraction of all Runtime scan results.
Download the Sysdig Vulnerabilities add-on from Splunkbase to get started, as described in Vulnerability Integrations | Splunk.
Non-Kubernetes Container Scanning
Scan Docker and Podman containers for vulnerabilities with Sysdig Secure.
For more information, see Non-Kubernetes Container Scanning.
Agentless Host Scanning (Technical Preview)
On AWS EC2 hosts, you can now perform agentless runtime vulnerability scanning. You can also view all discovered hosts, get real-time status updates, and troubleshoot issues with the Cloud Hosts page in Data Sources.
See AWS Agentless Installation for details.
Risk Spotlight (General Availability)
The Vulnerability Management team is excited to announce the official release of Risk Spotlight (aka EVE or “In Use”). After several iterations of the agent, profiling service, and vulnerability management integration stages to address accuracy and computational requirements, the Risk Spotlight service is officially GA.
With Sysdig agent v12.15+ and runtime vulnerability management scanning, you can identify and prioritize packages that are both vulnerable and actively “In Use” in runtime workloads.
We also enable external integrations with partners that use this data, such as Snyk and Docker.
See Risk Spotlight (In Use) and Risk Spotlight Integrations for details.
Leverage Artificial Intelligence for AWS Console Login Anomaly Detection
With the AWS Machine Learning (ML) policy, you can detect anomalous AWS Console login events in connected AWS cloud accounts.
This policy allows you to understand why an event is considered anomalous compared to the expected behavior. In addition, you get visibility into the most influential contributing factors and the confidence level of the detection accuracy.
For details, see the AWS ML Policy documentation.
Extend Posture to Use Auto-Remediation with AWS Cloud Resources
This feature allows you to automate the process of maintaining and improving the security and compliance posture of your AWS infrastructure, reducing the risk of security breaches and operational disruptions. This extends remediation to AWS Terraform resources.
First, create Terraform configuration files that define the desired state of your AWS resources. Sysdig provides automated remediation for fixing risks by opening a pull request (PR) directly on the IaC code files for your acceptance.
For details, see Compliance – Evaluate and Remediate.
RBAC Permissions in Posture for Accept Risk, Open PR
Administrators can now define granular role permissions to allow risk acceptance and opening pull requests for posture/compliance findings. These permissions have been retroactively added to the existing default roles of Team Manager and Advanced User.
For details, see Detailed Role Permissions.
Runtime Threat Detection Rules
Our Threat Research team has released several versions of the rules in the last month, including 31 brand new rules. Additionally, older rules have been deprecated. Below are the release notes for the most recent rules changes.
https://docs.sysdig.com/en/docs/release-notes/falco-rules-changelog/
Rule Changes
- Added the following rules:
- Query to Window Management System Detection
- Suspicious Access To Kerberos Secrets
- Service Discovery Activity Detected
- Access to Clipboard Data Detected
- SES Attach Policy to Identity
- SES Update Identity Policy
- SES Delete Identity Policy
- Task Scheduled with Highest Privileges
- Password Policy Discovery Activity Detected
- Hide Process with Mount
- Modify Grub Configuration Files
- Simple Email Service (SES) Verify Identity
- SES Update Account Sending
- SES Delete Identity
- SES Create SMTP
- SNS Delete Subscription
- SNS Delete Topic
- SNS Get SMS Sending Information
- Organization Update Service Control Policy
- Organization Create Service Control Policy
- Organization Delete Service Control Policy
- Repository Fork Set to Public
- Repository Fork Set to Private
- Attach SES Policy to User
- Auditd Logging Commands
- Repository Fork Set to Public
- Ransomware Filenames Detected
- New GitHub Action Workflow Deployed
- Okta Multiple Application Requests with Invalid Credentials
- Push on Github Actions Detected
- Okta MFA Bypass Attempt
- Deprecated the following rules:
- Malicious process detected
- Creation attempt Azure Secure Transfer Required Set to Disabled
- Azure Access Level creation attempt for Blob Container Set to Public
- Azure Blob Created
- Azure Blob Deleted
- Azure Create/Update a Storage Account
- Azure Delete a Storage Account
- Azure Delete Function Key
- Azure Create/Update a Storage Account
- Azure Create/Update a Storage Account
Default Policy Changes
- Added the following rules:
- Query to Window Management System Detection
- Suspicious Access To Kerberos Secrets
- Service Discovery Activity Detected
- Access to Clipboard Data Detected
- Password Policy Discovery Activity Detected
- Hide Process with Mount
- Modify Grub Configuration Files
- Ransomware Filenames Detected
- New GitHub Action Workflow Deployed
- Okta Multiple Application Requests with Invalid Credentials
- Push on Github Actions Detected
- Okta MFA Bypass Attempt
- SES Attach Policy to Identity
- SES Update Identity Policy
- SES Delete Identity Policy
- Updated the policy for rules:
- Ransomware Filenames Detected
- Contact K8S API Server From Container
- nsenter Container Escape
- AWS CLI used with endpoint url parameter rule
- Ransomware Filenames Detected
- Azure Blob Created, Azure Blob Deleted
Sysdig Monitor
Sysdig Default Pricing for Cost Advisor
Cost Advisor will now use Sysdig Default prices in instances where pricing information is unavailable, such as when viewing on-premises Kubernetes clusters. Additionally, Cost Advisor has been enhanced to help you identify the billing profile associated with a specific Kubernetes cluster.
Embedded Images in Metric Alert Notifications
Alert Notifications sent to Slack, email, and Pagerduty will now include a visual snapshot of the time series data that triggered the alert rule. This means less dashboard hunting at 2AM and the ability to snooze or escalate without opening your laptop.
 |  |
Group Outlier Alerts
Take advantage of the new Group Outlier alert type to detect anomalous behavior. Utilize Group Outlier alert rules to spot any hosts that are acting differently from the usual group patterns, or to highlight unusual patterns in operational metrics.
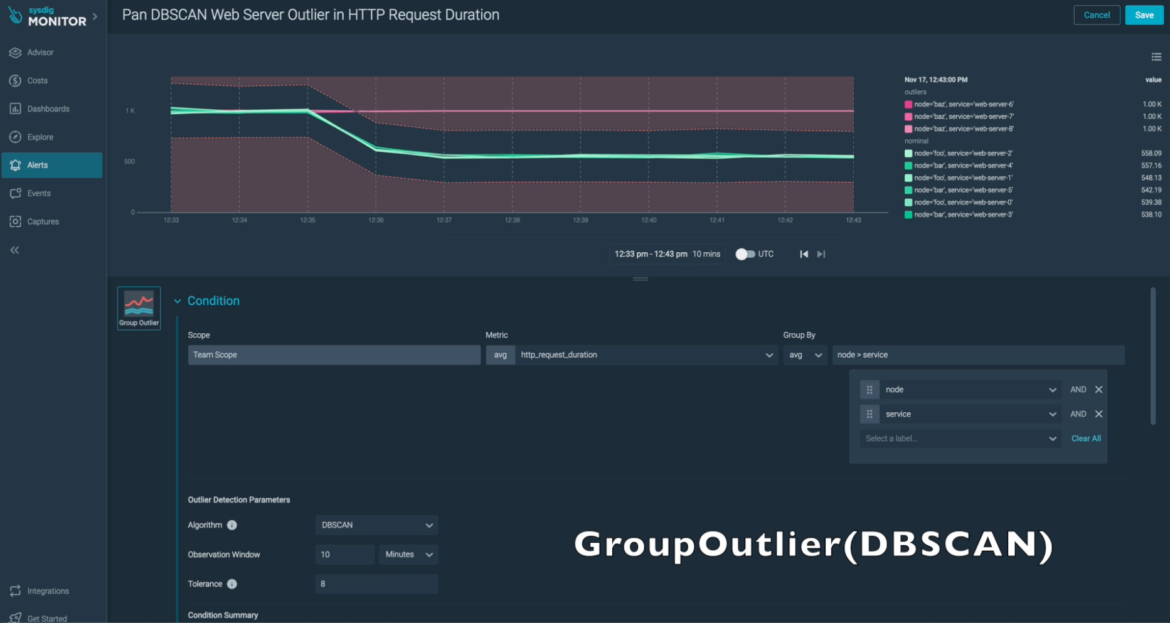
Sysdig Agents
12.19.0, December 2023
Feature Enhancements
Changed HTTP Health Endpoint to Bind to Localhost
Changed the HTTP health endpoint to only bind to the localhost interface. If you are using Helm, upgrade to the Sysdig Agent Helm Chart v1.18.2 or higher. For more information, see Agent Health.
Export Additional Agent Health Metrics Using Prometheus Exporter
The Sysdig Agent can now use a Prometheus exporter to expose additional agent health metrics. For more information, see Agent Health.
Due to the sensitive nature of some of these metrics, you may want to ensure that the Prometheus exporter endpoints are not exposed outside of your cluster.
Added Profiling Fingerprint Generation to Secure Light Mode
You can now enable Profiling in secure_light mode by setting the falcobaseline.enabled parameter to true in the dragent.yaml, or by specifying –set agent.sysdig.settings.falcobaseline.enabled=true if you install the agent via Helm chart.
Modified Audit Tap Message Delivery Policy
Audit Tap messages are now delivered even if they contain only file access records.
Defect Fixes
Improved Health Monitoring for Agent Subprocesses
Health monitoring for agent subprocesses now covers all subprocesses spawned.
Added Socket Timeout for the Proxy Connection to the Collector
Sysdig Agent now utilizes a socket timeout when connected to the collector via proxy. This allows the connection to recover faster without an agent restart when an issue occurs.
Reports Correct Values for Container CPU Usage in Kubernetes v1.26
Resolved an issue that impacted the calculation of CPU usage for containers in Kubernetes v1.26.
Detect App Check Metrics
Sysdig Agent now can successfully detect app check metrics. This fix enables SCM_RIGHTS to transfer file descriptors across all types of processes. Previously, if a file descriptor transferred via SCM_RIGHTS was for a socket serving app check metrics, the agent could not detect and query it for app check metrics. This presented missing app check metrics after a process reload.
SDK, CLI, and Tools
Sysdig CLI
v0.8.2 is still the current release. The instructions on how to use the tool are available at the following link:
https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
Python SDK is still at v0.17.1. More details on leveraging this tool can be found at the following link:
https://github.com/sysdiglabs/sysdig-sdk-python
Terraform Provider
We have just released the 1.20.0 version of Terraform provider. This release includes:
- Add group outlier alert type
- Support sidecar mode for serverless-agent (disabled by default)
- Switch to agent-kilt 0.0.2 for serverless-agent
https://docs.sysdig.com/en/docs/developer-tools/terraform-provider
Terraform Modules
- AWS Sysdig Secure for Cloud remains unchanged at v10.0.9
- GCP Sysdig Secure for Cloud remains unchanged at v0.9.10
- Azure Sysdig Secure for Cloud remains unchanged at v0.9.7
Falco VSCode Extension
v0.1.0 is still the latest release.
https://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0
Sysdig Cloud Connector
New Cloud Connector changes to (v0.16.59) under helm chart 0.8.8.
Admission Controller
New Admission Controller release (3.9.36) under helm chart 0.14.17.
Sysdig CLI Scanner
Sysdig CLI Scanner latest version is v1.6.3.
https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Sysdig Secure Inline Scan Action
The latest release is v3.6.0.
https://github.com/marketplace/actions/sysdig-secure-inline-scan
Sysdig Secure Jenkins Plugin
The Sysdig Secure Jenkins Plugin remains at version v2.3.0.
https://plugins.jenkins.io/sysdig-secure/
Prometheus Integrations
Prometheus Integrations has been updated to v1.24.0. This release contains updates to KEDA & OPA integrations.
Open Source
Falco
Falco 0.36.2 is still the latest stable release:
https://github.com/falcosecurity/falco/releases/tag/0.36.2
New Website Resources
Blogs
How Financial Services Organizations Can Stay Compliant – Without Sacrificing Security
Fuzzing and Bypassing the AWS WAF
Honeypots with vcluster and Falco: Episode II
Sysdig Stands Alone: GigaOm Names Sysdig a Leader and Outperformer for Cloud Workload Security
Webinars
SEC’s Cyber Wake-up Call: The Evolving Role of the CISO
Banking on Security: Defending Against Cyber Threats and Regulatory Demands
Generate This: Bringing AI to Cloud Security
Navigating Cloud Threats: The Art of Swift Detection and Response
Securing Success: Saiyam Pathak’s 2024 Guide to CKA and CKS Certification
How to Stop Cloud Attacks in Real-Time with Runtime Insights
Every Second Counts: Delivering Secure, Compliant Financial Services in the Cloud
Sysdig Education
Detecting a Cryptomining Malware Attack with Falco and Prometheus


